1. Introduction
There’s no one-size-fits-all approach to adopting digital transformation. The road to embracing it can be long, winding, and filled with potholes and other hazards along the way. That’s why we often refer to digital transformation as a journey. This Digital Transformation Framework will serve as a map to help you navigate this road, taking in the steps and processes you need to consider and identifying some of the leading technology solution vendors that create digital workspace solutions along with other valuable resources.
Not every organisation will be at the same stage of their journey. Some may be just starting out, while others are nearing the end. You can join the journey at whichever stage your organisation is at.
One thing you need to be aware of is that the journey can be and should be continuous. We’re not saying it will never end exactly, but it should be viewed as a lifecycle. Even if you have completed, successfully implemented, and onboarded a solution, time will have moved on, and inevitably, so will technology and your business.
This means that you may need to review the needs of the business as market trends and customer demand may have changed. Or perhaps new technology is now available that wasn’t previously or was deemed not mature enough to adopt at the time. Whichever the case in question, you should continue reviewing, refining, and adapting as technology and business progress. If you stand still, then you run the risk of falling behind your competition.
In this framework, we have identified six steps to successfully navigate the transformation journey from beginning to end. These steps are depicted in the following graphic:
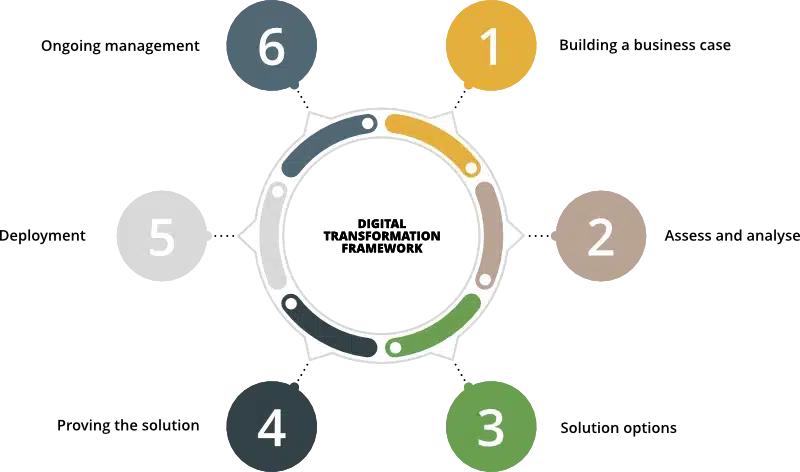
As previously discussed, you can start this journey from the beginning or jump in along the way, depending on where you’re in your own organisation’s personal journey.
What is digital transformation?
Before we start talking about how to enable digital transformation, let us take a minute to put this into context and explain more about what we mean by digital transformation.
At a high level, digital transformation can be described as…
“Adopting a digital-first mindset, taking advantage of digital-based technologies designed to create and deliver new business processes, to modify existing business processes, all with the end goal of delivering the best possible customer experience, drive employee innovation all designed to meet the ever-moving challenges of enabling an organisation to be agile and flexible to meet market demands and requirements and staying ahead of the competition.”
As you can see from the definition above, digital transformation is very much a change in mindset, moving from the old-school way of doing things to a digital-first mentality with a business-led approach to delivering technology that focuses on improving how an organisation works.
It isn’t just about deploying technology for the sake of technology because the IT teams are in the driving seat and want the latest and greatest technology.
Digital transformation is an opportunity for organisations to reimagine how they do business empowered by the latest technology solutions.
Even though we’re ultimately talking about technology solutions and how to deploy them, and we will discuss technology later in this framework, it is important to first understand why digital transformation forms a key part of any organisation and how that organisation should approach it.
We defined, at a high level, what digital transformation is in a generic sense, but in reality, it can apply to many different types of transformation. For example, it could be moving physical on-premises infrastructure to a cloud service provider, consuming subscription-based Software as a Service such as an HR system, adopting remote working policies, automating customer support services, or using AI-driven platforms to improve customer efficiency.
This particular framework will focus on remote working and how to deliver end user services, desktops, and applications to employees and external partners – The Digital Workspace or Digital Workplace. However, the processes we will discuss will be relevant to any digital transformation project. You just need to swap out some of the actual technology solutions for those relevant to you.
Six steps for successful digital transformation
Each of the six steps introduced earlier will be discussed in more detail as separate articles, but for now, we will summarise these to provide a high-level overview to help understand where your journey begins.
Business case
The first port of call for a digital transformation project or initiative, or for any project in reality, is to build a business case.
A business case is a sales pitch to the business and the key stakeholders or board members. Its purpose is to provide the information, to answer the “what?”, “why?” and “how?” questions required to decide whether or not the project gets the green light and investment in time and money. Ultimately, it needs to prove its value to the organisation.
This section will help guide you through building a business case and also understanding what a successful outcome would look like.
Assess and analyse
To be honest, the assessment and analysis phase could come before the business case in order to identify what is required. It will then be used to build a picture of what you have in place today and then again at every step along the way to ensure you’re refining as you go.
This section will detail the different nuances of assessing and analysing, from the initial business case to conducting a full-blown assessment of your current environment and the tools that can be used to enable this.
A critical part of this phase is the human element and employee and customer interaction.
Solution options
When your business case has been signed off, and you have a comprehensive picture of your current environment, you can now evaluate the available technology solutions to ensure you match the right solutions to your use cases to achieve a successful outcome.
This section will discuss the digital workspace solutions and the vendors in this space, guiding you through why you would choose one technology solution over another to decide which technology will address your requirements, ready to move on to proving the technology delivers against the requirements.
Proving the solution
Armed with the business case, assessment data, and your choice of technology, now is the time to put that solution to the test, measured against specific and scoped success criteria.
This section will guide you through proof of concepts and pilots and how to approach each phase of proving the technology isn’t only fit for purpose but also delivers the desired outcome.
Deployment
You have now proved the technology is fit for purpose and delivers against your success criteria and the business and use cases.
The next step is to take the lessons learned in the previous phases, particularly from the feedback gathered during the assessment and proving stages and put together an implementation plan from high-level design through to how to manage the onboarding process.
Management
Although this is the final phase of the process, in reality, it isn’t. It is just another important piece of your solution’s overall lifecycle and evolution.
With management, we will explore the day-to-day management options, from troubleshooting to fine-tuning and improving the end user experience. We will proactively take this information and feed it back into the business case and assessment/analysis phases discussed at the start of this framework to help continually identify requirements and evolve the solution with the demand of the business and as technology moves forward.

2. Building a business case
A project as far-reaching as digital transformation affects how a business operates and touches customers, employees, and anyone else working with the company. So, the first task to complete is writing a compelling business case. This comes long before any technical conversations take place and is purely a commercially led discussion.
The objective of the business case is a crucial step that enables you to secure the support, resources, and budget to move the project forward from the drawing board to reality.
Having a well-structured business case will help you justify, to the stakeholders, the investment required to deliver a successful outcome and should clearly outline the potential benefits transformation will bring in aligning and delivering the strategic business goals for your organisation.
Essential elements of your business case
The key to a successful business case is addressing all the questions around what, how, and why the digital transformation should gain support and ultimately be signed off. The business case should follow the steps outlined:
1. Executive summary
The starting point for your business case is the executive summary. Note the word “summary”. It should be a concise and to-the-point document that gives the stakeholders a high-level overview of the digital transformation initiative, what objective you’re trying to achieve, and the expected benefits.
For example, with a digital workspace initiative, the overall objective could be to allow employees a more flexible approach to working, which would benefit employee well-being and productivity.
2. Introduction
The introduction should build on the executive summary and go to the next level of detail. As part of this, you should provide context for the project. Explain to the stakeholders why the project is necessary. Include information about current market trends for your particular business, competitive pressures, and how you enable your business to stay relevant and get ahead.
It’s not only the external factors that come into play. You need to factor in any internal challenges that would benefit from digitalisation, such as attracting and retaining employees
3. Objectives
Objectives must be clearly stated and precisely what the digital transformation initiative aims to achieve. What are you trying to achieve exactly, and more to the point, why?
For example, an objective might be to provide a platform for employees to work remotely. The reason being to provide employee flexibility in working times and locations but also to tap into talent pools that can’t usually be considered due to personal circumstances such as potential employees not being near your office locations
4. Scope
Defining the project’s scope will highlight the business processes that are in focus for the initiative and who will be directly impacted by change. The scope needs to be clearly defined and documented. It needs to detail exactly what and who will be included in the project. You also need to be clear on the areas that won’t be included.
For example, the project might be directed at a particular department where remote working or taking advantage of a cloud-based SaaS application is the objective
5. Business needs and drivers
Now that you have understood the initiative’s objective and who it will directly affect, the next step is to match these against the needs of the business and what is driving the digital transformation. This brings into play the exec summary, introduction, objectives, and scope.
Considering all of these will help define what exactly the business needs and the drivers behind that need or requirement. For example, the scope will have defined who this project affects, such as the sales teams. In this case, the sales team may need access to some form of CRM tool or the ability to place orders and check stock in real time. The driver for the business being the ability for the sales team to have immediate access to accurate information and close sales quickly.
6. Benefits and ROI
We already touched on describing some of the high-level benefits identified with the business needs and drivers, but now you need to expand on these and go deeper.
This next level of detail should include things such as improvements to the customer and employee experience, increased efficiency and productivity, and cost savings, which will all result in revenue growth.
When it comes to the return on investment (ROI), you should compare and quantify the projected benefits with the project’s estimated costs.
7. Risks and mitigation
All projects have their risks. Although it might sound negative and counterproductive to building a business case, it is important to identify any potential risks and challenges that could be encountered throughout the project. Document these potential risks and plan to help mitigate them. You can start with some of those that are more common so you can pre-empt them and have a solution to solve them.
For example, initiatives involving employees and how they work often result in pushback. Have information prepared that will show how to resolve these employee pushbacks. We will discuss one way to mitigate some risks in the assessment document and get employees engaged in the project early to avoid such pushbacks.
Of course, there will be some risks that you could encounter along the way. Obviously, these risks are unknown at this stage but at least have a plan to deal with them.
As part of the risk and mitigation process, you should understand how to develop business continuity and disaster recovery plans. What would be the cost to the business if IT systems were unavailable? Could the company tolerate a day without them, or is it just hours before it affects the bottom line? Ultimately, these plans will form part of the architecture design to implement systems that ensure minimal downtime. However, the business case should identify these to help with any additional budget conversations to enable the availability of systems but also balance the cost of implementing these versus any losses incurred.
To quantify this, it is worthwhile conducting risk assessments and business impact analysis to determine the criticality of various business functions and processes and understand what the most downtime and data loss each of these business areas could tolerate.
Having a robust disaster recovery plan in place is crucial for the business to minimise downtime, protect data, and ensure business continuity in the face of unforeseen disasters. It helps you recover more quickly and efficiently, reducing the financial and operational impact of disruptions.
The business case should cover this as additional systems, infrastructure, and processes may be required, which could add to the project budget to ensure this is factored into the design stages.
8. Project timeline and milestones
At this stage, the business case doesn’t need a detailed project plan. That can come once you have sign-off. What is required is a high-level timeline for the project and an estimation of how long each project phase will take.
It is important to include any major milestones and key deliverables in this timeline. That allows the business to see that progress is being made and the project is on track. Don’t say that the project will take three years and then show the business the solution on the very last day.
Delivery and onboarding, as we will discuss later, should take a phased approach and, more importantly, communicated to the business at every step along the way.
9. Budget and resource requirements
A key requirement to get financial backing is to agree the budget as part of the business plan.
Taking the scope, objectives, and project timeline will help with the budgetary requirements. For example, you should understand the number of people required at each step and the skill sets needed. This will help define the cost of employing those people, training them, and filling any gaps with external contractors. Of course, you’ll have people in your organisation, but you need to factor in the cost to the business if you pull them away from supporting the business daily.
As part of the research for writing the business case, you will have an idea of the requirements needed to put together costs for technology, such as additional hardware, software, or subscription costs to deliver the complete transformation project.
Armed with information, you can explain how the budget aligns with the expected benefits and ROI.
10. Technology solutions
Now, we can have our first introduction to technology. However, this should not be a deep-dive architecture design or start to discuss specific vendors and specific products. It should include specific technologies or solutions that will deliver the digital transformation brief and objective.
For example, the technology solution could be a remote working solution, a bring-your-own-device initiative, or using some form of cloud-based software via a subscription. Depending on the scope, you’ll know what departments this is aimed at – it may be HR software for managing people or account software for managing finance and payroll.
11. Change management and adoption
As we’re talking about digital workspace solutions that will be widespread throughout your organisation, you need to have an adoption plan for onboarding people and phasing in the potential new way that both employees work and customers do business with your organisation. Remember, people fear change, and human nature is to carry on working the way they are.
This plan should clearly explain how to manage any cultural and organisational changes arising from digital transformation. Ensure the business case covers training, communication, and stakeholder engagement strategies. For example, get HR engaged early on with working-from-home strategies and employees’ rights and entitlements.
12. Governance and project management
How is the project going to be governed and structured? You need to clearly describe roles and responsibilities. Identify key personnel and their role in delivering the project.
How is the project going to be managed on a day-to-day basis? Identify and adopt a proven methodology. That may also come under the resource requirements in that you have people qualified to deliver that methodology.
For example, you could use ITIL, Prince, and to develop the solution an Agile Scrum methodology. These must be identified to instil confidence in the stakeholders that the project won’t be derailed.
13. Measuring success
Measuring success isn’t just about getting to the end of the project and demonstrating that you have delivered what you said you would. Of course, that’s the desired outcome, but it is also about how you get there. By that, we mean defining key performance indicators (KPIs) and other metrics that will be used to measure the success of the digital transformation.
This is particularly key with digital workspace solutions. For example, it is very easy to set up a platform to deliver applications to end users. So, in that instance, the project is delivered if that’s the objective. But is it? You need to have a plan to measure the feedback from the people using the system, whether it delivers what they need to get the job done, and whether it delivers the performance. Ultimately, there’s no point in delivering something that isn’t useable in the real world. This should not be left up until the end. It should be an ongoing process aligned with the milestones set.
Clearly explain how you will track progress and demonstrate the results and how this will be fed back to the stakeholders.
14. Conclusion
This is what we affectionately call the “News at 10” approach.
“Tell them what you’re going to tell them, tell them, and then tell them what you told them!”
At the beginning, clearly state the goals and objectives of the project as a high-level summary. Then, summarise the key points of how you set out the business case and the steps to deliver it. Finish by reiterating the objectives and the importance of the digital transformation project and what it would mean for the organisation.
15. Supporting information
As proof points along the way, and to bolster why you’re proposing this business case, make sure to include supporting documentation. This could be market research on other similar organisations that have taken a similar approach to the one you’re proposing or market trends and observations such as Gartner, IDC, or Forrester reports. Look at some of the vendors you might be looking for for documented case studies and ROI statements.
This will reinforce why your organisation should adopt the proposed solution.
16. Executive presentation
Once you’ve completed the business case, before simply handing it out to the stakeholders to read themselves, plan a meeting to present the business case. This ensures they fully understand what you’re proposing and don’t misinterpret anything that wouldn’t garner their support.
However, don’t just read it out at the meeting. Create a concise executive presentation by way of introducing the written business case. Use it to ensure you present the most impactful and important points as to why this project should go ahead. It also allows the senior leadership, decision-makers, and stakeholders to ask questions that can help tighten up the business case when answered. After all, if you include some of their thinking, they can hardly object to the project moving forward!
17. Review and sign-off
After you’ve presented the business case and allowed the stakeholders time to review it in more detail, ask any questions, or clarify any outstanding points, you can move to get the business case signed off and the budget approved.
However, it doesn’t end there just because the business case is approved. You should now use it to serve as a roadmap that can be used to guide the transformation through the project phases from assessment, planning, design, and finally, implementation.
Ensure you refer back to the business case and the stakeholders for the ongoing measurement of delivering a successful transformation. Ask yourself the following. Is the project on track to deliver what you set out to deliver? Is it still relevant to the business? Have things changed? All of this may need to be factored in, and the business case updated to reflect any changes.
You now have your tried and tested framework and guide to building a successful business case.
Of course, this serves as a guide based on experience in delivering digital workspace transformation projects from inception to implementation.
There may be other areas you need to discuss that are only relevant to your particular industry sector.

3. Assess and analyse
You have now, at this stage, successfully secured the support to start the project. The stakeholders are on board, and more importantly, you have the budget secured. So, what’s next? Where do you start? The purpose now is to push forward and look at potential solutions that meet the objectives set out in the business case.
However, it is essential to understand the current environment before you can fully understand what is required. You will have already identified the high-level objectives of why you need the digital transformation, as that formed the basis for the business case, but do you really know, at a detailed level, the systems and processes currently in place? After all, it is difficult to tackle the unknown. Not only that, but you also need a starting point from which to measure progress and success. Call this a baselining exercise, if you will.
We’re going to look at two elements: technical and human. This will enable you to build that picture of today and take that as the baseline to allow you to move forward. So, what are the technical and human elements you need to assess and analyse?
The technical element
You need to understand your current infrastructure regarding resources and locations. For example, how many servers, what are they running (OS and apps), and how much overhead do you have? Also, where are your physical locations, and how are they connected?
The human element
You need to understand how people currently work. Where do they typically work from now, and what devices do they use? Do they have any specialised hardware and software they use that will still needed after the transformation?
To help you gather this information, we’re going to look at these in more detail and highlight tools available that not only help with the assessment phase but tools that can continue to be used to help monitor the new environment and ensure it is still meeting the objectives.
The technical assessment
In the world of digital workspace transformation, the assessment will often be referred to as a desktop assessment. However, it goes deeper than just the desktop. You need to use this project phase to onboard your employees to map out their entire life cycle through infrastructure. Not just a snapshot of what they were doing at the time the assessment data was captured.
Ultimately, you want to continually assess your employees’ experience so that you can ensure they have the best user experience possible. In the long run, this will lead to fewer support calls and more productive employees as you can proactively understand what is happening throughout their working lifecycle within the organisation, especially as they grow with the business and their requirements change.
But for today and the here and now, we’re focusing on that very first step – onboarding and the initial assessment so as to draw that baseline from which to move forward.
The question then is, what exactly is involved in this assessment and what is required? It comes down to several things that we’re looking for. This includes examining your current desktop landscape by gathering key metrics to understand what is currently being delivered, who it is being delivered to, and more importantly, how resource-intensive it is.
The likely outcome is that User ‘X’ has a Windows 10 desktop, with a particular CPU of which a certain percentage is consumed. Plus, similar metrics for memory and disk space. Network utilisation is also a key measurement of determining how much bandwidth the end user is consuming and if they’re suffering any latency issues. We need to build a picture of everything going on for User ‘X’ and all end users in your organisation.
One point to note here is that we’re not just talking about physical desktops. It may well be that an organisation already has virtual desktops and is looking at the next generation. Or you have a hybrid deployment of both. Either way, the assessment is key. What other key metrics we’re looking for in the assessment data:
- Which users use which applications (when, from where, and how often?)
- Unsuitable applications/use cases for delivering the outcome defined in the business case.
- Legacy applications and operating systems
- Which client operating systems are being used?
- What type of devices are currently being used?
- Hardware inventory of existing devices – clients, peripherals, infrastructure
- Machine boot times and login process breakdown
- Current delivery methods (RDSH, XenApp, VDI, physical PCs, and so on)
- User profile details
As we have said, the end goal of this phase is to create a baseline of what your environment looks like today. You then have a good understanding of how to move forward and, more importantly, understand any blockers to achieve the end goal. You may need to revisit the business case as you uncover something that may require a slightly different approach to what was initially envisaged. Better to get that on the table sooner rather than later so as not to miss those all-important project milestones.
At the end of this phase, you will have created a baseline as a reference point to demonstrate progress and to help shape and define the next phase of looking at technology solutions. The assessment could throw up something that means one particular technology solution is unsuitable. Equally, it could open the door for other solutions you thought might not fit the bill.
Don’t forget that the physical data and metrics are only half of the story. You still need to understand the human elements and what employees want and need to build the complete picture.
Technical assessment tools
Manually collecting data metrics is a herculean task, but numerous tools can help you with this exercise.
One important thing to note is that these tools aren’t one-hit wonders and deliver more than just the assessment data. They will also be used throughout the lifecycle of the production solution, continuously monitoring and managing the overall end user experience and proactively alerting you to any issues. Therefore, these tools are one of the first things that you will deploy and demonstrate value to the business. This is, in reality, your first milestone.
ControlUp is a monitoring software company that provides tools and solutions used to manage, monitor, and analyse virtual and physical desktop and application performance.
- ControlUp Real-Time Monitoring and Insights
- ControlUp for Citrix, VMWare, RDS, AVD
- Scoutbees Proactive cloud-based monitoring
- Realtime DX
- Edge DX
- Automation
- Remote User Monitoring
- Historical Data and Analytics

Liquidware Stratusphere UX is a digital experience monitoring and diagnostics solution delivering comprehensive visibility across platforms, including VMware Horizon, Citrix Virtual Desktops and Apps, Microsoft Azure Desktops or physical desktops
- Login breakdown
- Process optimisation
- Health and security monitoring
- Realtime DX
- Connectivity
- Infrastructure monitoring
- Remote User Monitoring
- Historical Data and Analytics

Lakeside’s digital experience management platform helps you proactively measure, analyse, and optimise your employees’ digital experience anywhere they’re working.
- Availability and performance monitoring
- Root cause analysis and prevention
- End-user productivity
- Reduction in volume of it incidents and tickets
- Desktop virtualization migration
- IT automation via bots
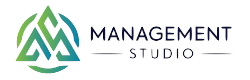
Management Studio helps organisations to plan, manage and execute large IT transformation programmes.
The solution directly integrates with existing systems, such as Microsoft Active Directory (AD) and Microsoft End Point Configuration Manager (MECM), to create a rich profile of users and assets within your organisation. Data points from each of the source systems are layered to create a contextual view of what users do, their place in the organisation, and how assets are utilised. It also tracks changes to all objects as they happen to ensure everyone using the tool has current and relevant insight into the estate
- Details required for packaging such as location of the installation media and instructions, pre-requisites, application behaviour and post-installation activities.
- A user’s hardware and software requirements
- Which users should have access to a particular application.
- License and support agreements that are in place for specific assets.
Assessing the human element
Phase two of the assessment phase doesn’t require any specific tools. At least nothing that needs to be installed to gather actual data metrics.
Instead, it should be conducted by interacting with actual end users; the tools required are the ability to speak to them.
It is good to start this interaction early on in the project as you will need these people at various steps along the way in trialling and piloting, so now is a good time to get them onboard.
Being a part of the IT team will give you a good understanding of the tasks that users undertake and the software they use to achieve them daily. However, while you may be able to name applications, do you actually understand how they work from the perspective of the person using them daily?
Talking to the people using the current systems serves two purposes. First, it gives you something to measure the accuracy of the data from phase one. Do the two match up, or is there a mismatch somewhere? You need accurate information to make the project successful. Wrong information equals the wrong answer, i.e., the wrong solution!
Secondly, it allows you to understand any challenges users currently have. It may be the usability of the current system, or they may suggest improvements that would increase usability and productivity
Applications
Understanding your current applications is a key part of the assessment phase. After all, this is what people use to perform their roles.
You will already have an inventory list from phase one, but now is the ideal opportunity to see what is actually being used and whether it is even the correct app. Understanding application usage and what the users are using daily is key. But you should also look out for other patterns.
For example, are there any shadow IT introduced SaaS-based apps that won’t show up on an inventory of installed applications? If so, you need to understand why that’s and how that gets fixed as part of the overall project. It may well be that the transformation project is to look at consuming more SaaS-based software, so maybe the users have resolved the problem. Now, you need to look at how it is managed going forward.
Another example is comparing a particular application from the phase one report versus the end user’s perspective. If the report states the app was used three months ago, you may think that means it isn’t being used and so can be removed. However, the users tell you that it is report software that’s only used once every quarter, hence the three months.
Then, there are Legacy or Heritage applications. Legacy is those older apps that can be upgraded, and heritage is those that have no upgrade path but are still business critical. This could present a problem with modern platforms, so you need to understand any upgrade paths and methods to still be able to run applications.
Performance and resources
You will have a set of performance figures and benchmarks gathered from phase one. Now is the time to get the end user’s perspective on whether that’s an accurate picture of performance and what the end user actually experiences.
The figures may suggest that everything is working well, enough resource has been allocated, and response times have been measured favourably. Still, the user might have a different opinion. This is particularly important when sizing a solution and ensuring sufficient resources are available. The last thing you want is potentially migrating poor-performing applications without improving the end user experience.
Understanding performance is all about rightsizing the new solution and understanding what is required. Oversizing means potentially more cost and more infrastructure depending on how it is hosted. Undersizing means potentially poor performance and unhappy users. It also may mean difficult conversations to secure more budget to bring the solution up to the requirements.
One key thing to bear in mind is growth during the solution’s life cycle. Businesses grow organically, or by mergers and acquisitions, so you need to factor in that growth. It could be 10% year on year. This is a question for the senior management to answer, and it allows you to align technology with their strategy.
Understanding end user experience
Above all else, what matters most is the end user experience, which is the measurement of how good or how poor the end user’s experience of using the solution is. If done correctly, the end users may not even realise it has happened. Instead, they will notice a marked improvement.
With a digital workspace transformation project that’s 100% focused on the end users, it is more likely that they will realise a change has happened, and you need to ensure that this is a positive experience for the project to be a success. To do this, you need to almost get inside the head of the end users for a “day in the life of…” style interaction to see how they use the environment today. The measurements of end user experience will be wide, varied, and often subjective. Still, they will include elements such as boot time, application load time, login time, page load time, app failures, and finally, how intuitive it is to use. This is something that assessment tools may well tell you, but experiencing it first-hand is a much better way of understanding it.
As you progress through the proof of concept (POC), pilot, and tuning processes, you must ensure that the user experience is constantly improving. Failing to consider end user experience will result in the project’s definite failure. To do this, you must interact with the end user community.
Floor walks, interviews, and department champions
So, how do you go about interacting with the workforce? As we outlined previously, and to reiterate, while performing data gathering assessments to collect data and metrics on your current environment are important parts of any EUC project, they should not replace the need to interact with people. The benefit of human involvement is that it allows you to pick up elements that wouldn’t be possible with software alone.
Start by simply walking through your offices, noting what the users are doing, what applications they’re using, what accessories, how many screens they use, if they’re using laptops or PCs, and so on. Ask them what is good and bad and how they’d improve on what they have today.
The upshot of this is you’re already, at an early stage, involving the people who will use the solution in building and shaping the transformation, so ensure you don’t get any pushback at crucial stages of the project.
User Groups, Steering Committees, and Department Champions
Form user groups or steering committees and perhaps nominate department champions. A department champion is an end user who will be the go-to person within the department for everything to do with their department’s desktop, design, testing, and support. They don’t need to be IT experts, but they should have a desire to help you improve the overall desktop experience. You should work with these champions to help design their desktops, as they will be your first port of call for testing, and then testing again after you have listened to and implemented any of the feedback.
By working with a department champion, you will have a sponsor within the department. They will have a sense of pride over what is being rolled out and will be there to help you shape the desktop and be the user on your side to help explain why certain decisions have been made.
The “assess and analyse” phase of the digital transformation is all about asking questions and gathering data. Invaluable data that’ll help you determine how your workforce consumes IT services.
As we’ve discussed, it’s not just about gathering the data from existing systems, which is important in its own right, but also taking on board the human element of how people work, what they need to perform their roles and also understand what works today and what doesn’t.
The knowledge of physical data and human data is invaluable in choosing the right solutions for your digital transformation initiative and guaranteeing its overall success.

4. Solution options
With the business case and justification signed off and the assessment and analysis complete, you now have a full picture. It’s time to examine the different options for delivering your digital workspace transformation project. We’ll start by looking at the generic types of solutions and what they mean before talking about the runners and riders, aka the vendors.
Solution types
By solution type, we’re talking about the overarching technology rather than a specific vendor and product. Taking this as a starting point means you can now start to map these solution types to your business case while at the same time ensuring you keep an eye on the data metrics to ensure that even while a solution type will work, it will scale to meet your specific requirements.
Not only will we talk about the solutions that deliver the end user experience, but we’re also going to look at the data centre infrastructure if on-premises is the way forward. We’ll also look at the endpoints – the devices your workforce and customers will use to connect and consume services.
Virtual Desktop Infrastructure (VDI)
Virtual Desktop Infrastructure or VDI is a technology that allows organisations to host and manage virtual desktops on centralised servers located in data centres or cloud-hosted platforms, which end users can access remotely.
It provides the end user with a full desktop experience, just like a PC or laptop, in that the end user will have a Windows 10, Windows 11, or Linux desktop. However, in the case of VDI, this’ll be a virtual machine hosted in the data centre rather than a local device on their desk.
Components of a VDI solution include:
- Hypervisor: VDI relies on a hypervisor, a software or hardware platform that creates and manages virtual machines (VMs). Each VM represents an individual virtual desktop.
- Virtual Desktops: Virtual desktops are the instances of desktop operating systems (e.g., Windows, Linux) running on VMs. These desktops are isolated from one another and run independently, allowing users to customise their environments.
- Connection Broker: A connection broker connects end users to their virtual desktops. It authenticates users and directs them to the appropriate virtual desktop resource. It also helps load balance and manage resource allocation.
- Storage: VDI solutions require ample storage to store virtual desktop images, user data, and system files. Storage performance is critical to ensure a responsive user experience.
- Network Infrastructure: A robust network infrastructure is essential for fast and reliable access to virtual desktops. High-speed, low-latency connections are particularly important for a smooth user experience.
- Display Protocol: The mechanism to deliver the screenshots across the network and to facilitate the end user interaction via keyboard and mouse. It’s also used to redirect USB devices from the endpoint device to the virtual desktop.
- End Point Devices: End users can access their virtual desktops from various devices, including traditional PCs, laptops, thin clients, tablets, and smartphones. They use remote desktop or VDI client software to establish connections and to deliver the end user experience. Often, a web browser can also be used.
- Desktop Templates: Administrators create and manage desktop templates or images, which serve as the basis for virtual desktop instances. These templates contain the OS, applications, and configurations.
- Resource Pooling: VDI systems typically pool computing resources (CPU, RAM, storage) to efficiently allocate them to virtual desktops as needed. This ensures that resources are shared among users dynamically.
- Security: Security is a crucial consideration in VDI deployments. Measures include access controls, data encryption, and user authentication to protect sensitive data and ensure compliance with security standards.
- Scalability: VDI allows organisations to scale their virtual desktop infrastructure up or down as needed to accommodate changes in user demand and seasonal work patterns.
Why VDI?
VDI offers several benefits, including centralised management, improved security, easier software updates, and the ability to provide remote access to desktop environments. It’s commonly used in scenarios where organisations must provide secure and controlled access to desktop environments for remote workers or where standardisation and consistency in desktop configurations are important.
Whereas VDI provides the user with a full-blown desktop experience from where they run their applications, application delivery or application publishing, as it’s more commonly referred to, delivers individual applications. You may also see this described as server-based computing (SBC).
Session-based applications are applications that run on server-class hardware in the datacenter or the cloud and where an instance of the application is launched as the end user logs in. Being server-based, the application can be launched multiple times on the hosting server and delivered to each end user that launches it. If you’ve more users than a single server can handle and want high availability, then you create a server farm to deliver the resources.
A session is a period of interaction or engagement between the end user and the application they launch.
Why Application Publishing?
You may have use cases within your business where an end user typically uses one or two applications. Delivering them a full VDI desktop might not be the most cost-effective or efficient way of delivering that.
With application publishing, you’re just delivering the applications they need. Nothing more, nothing less. All they can do is launch the applications that they’re entitled to.
Session-based desktops
Session-based desktops offer a mid-ground between a full VDI desktop and application publishing.
An end user is presented with what effectively looks like their desktop operating system. However, it’s just a session based on the operating system of the server that’s delivering it. As such, the end users cannot change or update any settings or configuration information. They can only launch the applications that are presented on the desktop.
As with application publishing, a single server, or server farm, hosts the desktop sessions, where a single server could host tens or even hundreds of end users concurrently.
Why Session-Based Desktops?
Again, as with application publishing, you may have use cases where an end user needs a desktop-like experience and has several applications they need or to have some interaction with the operating system.
Desktop as a Service
Desktop as a Service (DaaS) is a cloud computing service model that delivers VDI-based desktops or published applications to users via the internet.
Instead of running desktop operating systems and applications on local physical computers or traditional on-premises servers, as we’ve talked about with the models previously discussed, DaaS now moves these very same types of hosting mechanisms to a cloud provider’s data centre.
The solution is managed via a web portal that typically allows you to upload your OS images and applications and is charged on a consumption-based model. That means it’s subscription-based, pay-as-you-go billing. For example, a desktop of a particular specification could cost $30. If you add a hardware-accelerated graphics card, it could be $50. Sizing the solution is vital, as oversizing means you could be paying more than is necessary.
Why Desktop-as-a-Service?
DaaS is particularly attractive for businesses looking to simplify desktop management, reduce IT infrastructure costs, and support remote work and bring-your-own-device (BYOD) policies. However, the suitability of DaaS depends on an organisation’s specific requirements, security considerations, and budget constraints. For example, defence-based organisations may not be able to take advantage of DaaS as it cannot deliver desktops and applications at the required classification level.
DaaS is ideal for greenfield sites or SMB-type organisations with little or no on-site IT teams or who don’t want the overhead of managing infrastructure. However, many larger organisations are looking to DaaS to help reduce costs.
Hybrid
Hybrid isn’t another solution but a combination of the solutions we’ve already discussed. It means that an organisation may consume services of many different types and vendors.
For example, some infrastructure may remain on-premises, but you also deliver some applications from an as-a-Service platform. This might be down to the fact that different platforms have different strengths and costs. One may deliver a better solution for a specific user type, and another specialises in a requirement for a different department. You’re basically taking services from the leaders in each field.
What is key in this model is the management layer and bringing all those services together both from a management perspective and a cost perspective.
Why Hybrid?
This model allows you to consume services from different vendors. As we touched on, one service provider could deliver one key service and be the leader in that field versus a different vendor who is the leader in delivering another service. Hybrid allows you to take advantage of different solutions to meet your exact requirements.
Digital workspace portals
This is particularly useful when you’re delivering applications and desktops from several different platforms, such as when using the hybrid model, a workspace portal or an online storefront providing a central location and way for end users to access their resources.
End users will have access to their resources based on their entitlement, but these portals also let end users self-serve resources via the concept of an application catalogue. End users can select resources that they don’t currently have access to, which in turn starts an approval process for the IT teams to grant access, ensuring licenses are in place.
Why Digital Workspace Portals?
Digital workspace portals are aggregators for end users to access resources from one central location. This makes it easy for them to consume their resources. For IT teams, it means they don’t have to worry about how to get resources to the end users. They simply make them available to the end users via the portal.
Software as a Service
Software as a Service is a cloud computing model in which software applications are provided over the internet on a subscription-based pricing model. The subscription-based model means that your organisation will pay to use the applications monthly or annually.
Instead of purchasing and installing software on individual computers or servers, end users can access the software and its features using a web browser.
Why Software-as-a-Service?
Common examples of SaaS applications include customer relationship management (CRM) software, email services, office productivity suites (like Google Workspace and Microsoft 365), project management tools, HR tools, and accountancy solutions.
SaaS is a popular consumption model because it offers a more cost-effective and convenient way for businesses and users to access and use software applications quickly and easily without the hassle of traditional software installation, maintenance, and updates.
For a business, it also signals a move from a capital expenditure model (CAPEX) to an operational expenditure model (OPEX).
Delivery platforms
In this section, we will highlight some of the key and leading vendors in the digital workspace area and the type of solutions they offer.
VMware is a leader in delivering virtualisation and cloud computing technologies for both the data centre and the digital workspace.
VMware’s virtualisation technologies are widely used in enterprise environments to optimise resource utilisation, enhance scalability, improve disaster recovery, and reduce hardware and operational costs.
- VMware vSphere: The virtualisation platform that provides a comprehensive set of virtualisation and management capabilities for creating and managing virtual machines on physical servers.
- VMware ESXi: A core part of the vSphere platform, ESXi is a bare-metal hypervisor that allows you to run multiple VMs on a single physical server. It’s the foundation for vSphere and is used for server virtualisation.
- VMware Workstation: This is a type-2 hosted desktop hypervisor solution that allows users to run multiple operating systems on a single physical machine. It’s often used for development and testing.
- VMware Fusion: Fusion is similar to Workstation but designed to run virtual machines on an Apple Mac.
- VMware Horizon: This virtual desktop infrastructure (VDI) solution allows organisations to host desktop environments on servers and deliver them to end users. It can also deliver published applications. Horizon also has several other end user focused solutions designed to make the digital workspace more efficient and deliver the best end user experience:
- App Volumes: Delivers stateless applications to virtual desktops.
- Dynamic Environment Manager: Delivers end user personalisation and policy configuration of the desktop.
- Horizon Cloud: Delivers virtual desktops and hosted apps as a cloud service that can be delivered to any device, anywhere.
- Workspace ONE: Management platform that allows IT administrators to centrally control end users’ mobile devices and cloud-hosted virtual desktops and applications from the cloud or from an on-premises deployment.
- Workspace ONE Unified Endpoint Management (Previously AirWatch): Mobile Device Management (MDM) platform for managing, onboarding, and enrolling end users.
- VMware NSX: NSX is a network virtualisation platform that allows you to create and manage virtual networks. It’s used for software-defined networking (SDN) and network security.
- VMware Cloud: VMware Cloud services enable you to integrate, manage, and secure applications on cloud resources. These services work for any cloud service using the VMware virtualisation platform.
Citrix is now part of the Cloud Software Group and specialises in providing software and technology solutions for virtualisation, cloud computing, and remote access. Their products and services are primarily focused on enabling organisations to deliver applications, desktops, and data to end users securely and efficiently, regardless of their location or device.
Citrix technologies are widely used in various industries and are particularly beneficial for remote work, business continuity, and simplifying IT management.
- Citrix Virtual Apps and Desktops: This solution allows organisations to deliver virtualised applications and desktops to end users, providing them with a consistent experience across different devices and locations.
- Citrix Workspace: A digital workspace platform that integrates various Citrix technologies and services to provide users with a unified and secure experience. It includes features like single sign-on, secure access to applications and data, and collaboration tools.
- Citrix Endpoint Management: Manage device and app policies and deliver apps to end users. Business data remains protected with strict security for identity, devices, apps, data, and networks.
- NetScaler: An application delivery and load balancing solution that optimises the performance and security of applications and services. It can also be used as a secure gateway for remote access.
- XenServer: A virtualisation platform that allows organisations to create and manage virtual machines.
- Citrix Cloud: Citrix Cloud is a cloud-based management platform allowing organisations to manage and deploy Citrix solutions from the cloud, simplifying infrastructure management.
The Microsoft name is synonymous with end user computing and digital workspace solutions. It’s safe to say that most organisations will be using the Microsoft Windows operating system and also their office productivity applications such as Microsoft Office or Microsoft Office 365.
- Microsoft Windows: The company is best known for its Windows operating system, which is used on the majority of personal computers worldwide.
- Microsoft Office: Microsoft Office is a productivity software suite that includes applications like Word, Excel, PowerPoint, and Outlook. It’s widely used in business and personal settings.
- Azure: Microsoft Azure is a cloud computing platform that provides various cloud services, including computing, analytics, storage, and networking.
- Microsoft 365: A subscription-based service that combines Windows operating systems and Office 365 alongside other packaged software-as-a-service solutions.

Inuvika provides a simplified, less complex, and more cost-effective alternative to the VMware and Citrix platforms. The Inuvika OVD solution provides a delivery platform for applications and desktops using on-premises or cloud-based infrastructure. Windows and Linux apps and desktops can be delivered to any client device or via a web browser.
- OVD Enterprise: Delivers critical business applications through a fast and secure digital workspace experience. With several delivery modes, you can choose the format that’s most familiar to your end users.
OVD Enterprise can be installed in your data centre or any public cloud data centre. It deploys quickly, has a single easy-to-use admin console and is as little as half the cost of virtual app or virtual desktop alternatives.

Amazon Workspaces is a cloud-based service provided by Amazon Web Services (AWS) that allows organisations to create and manage virtual desktops for their employees.
It’s a part of Amazon’s broader cloud computing services and is designed to make it easier for businesses to provide remote desktops and applications to their workforce.
- Amazon AppStream: AppStream 2.0 is an AWS End User Computing (EUC) service that can be configured for SaaS application streaming or delivery of virtual desktops with selective persistence.
When AppStream 2.0 is used for virtual desktops, saved files and application settings remain persistent between user sessions, and a fresh virtual desktop is assigned to the user every time they log on.
Google Workspace, formerly G Suite, is a cloud-based productivity and collaboration software suite developed by Google. It includes various productivity and communication tools for businesses and organisations to use. Some of the core applications and services included in Google Workspace are:
- Gmail: A professional email service with a custom domain, spam filtering, and integration with other Google services.
- Google Drive: A cloud-based storage and file-sharing service where you can store documents, spreadsheets, presentations, and other files.
- Google Docs: A web-based word processing application for creating and editing documents.
- Google Sheets: A web-based spreadsheet application for creating and editing spreadsheets.
- Google Slides: A web-based presentation application for creating and editing slideshows.
- Google Forms: A tool for creating online forms and surveys.
- Google Calendar: A calendar application for scheduling and managing events and appointments.
- Google Meet: A video conferencing and online meeting platform.
- Google Chat: A messaging and collaboration tool for team communication.
- Google Sites: A website-building tool to create and manage websites, intranets, or project sites.
- Google Keep: A note-taking app for capturing and organizing ideas and information.
- Google Vault: A tool for archiving and managing emails and other data for compliance and e-discovery purposes.
Google Workspace offers various plans to meet the needs of businesses and organisations, including small businesses, education, and enterprise-level customers. It’s a popular choice for companies looking to enhance productivity, collaboration, and communication while relying on Google’s cloud infrastructure.
Infrastructure
In this section, we’ll highlight some key and leading vendors who deliver the infrastructure platforms designed to support digital workspace solutions.
HPE focuses on providing a wide range of technology products, solutions, and services to businesses, governments, and other organisations. The company’s offerings span various areas of the IT industry and include servers, storage, and networking solutions.
In addition to the hardware, HPE also offers cloud services with GreenLake. HPE GreenLake is a flexible, consumption-based IT service designed to help organisations transition to a cloud-like IT consumption model while maintaining on-premises control and security.
GreenLake provides a cloud-like experience for on-premises infrastructure and services. It allows businesses to consume and pay for IT resources based on their actual usage rather than making large upfront capital expenditures. There’s a specific GreenLake offering for delivering VDI.
Dell Technologies caters to a wide range of customers, from individual consumers to small and medium-sized businesses to large enterprises. The company’s products and services encompass hardware, software, and IT consulting services.
As part of the Dell portfolio, they offer validated designs for delivering virtual desktop infrastructure, including Microsoft, Citrix, and VMware.
Dell also has a portfolio of cloud-based solutions under the Apex umbrella, enabling you to deploy VMware and Microsoft cloud platforms.
Thin clients
In this section, we’ll highlight some of the key and leading vendors who provide end point thin client devices designed especially for digital workspace solutions.

Amulet Hotkey is a company that specialises in providing innovative solutions for remote and virtualised computing environments.
They offer a range of products and services designed to improve efficiency and flexibility in IT operations, particularly for finance, healthcare, and manufacturing industries. Solutions include end point client devices, a range of optimised servers, and PC-based remote solutions, including KVM and host extender cards.
Client devices are OS agnostic and have the unique ability to support a fibre-based network connection, which is ideal for secure environments.

IGEL provide a managed OS for the endpoint that enables secure access to any digital workspace. They also offer an enterprise management solution for managing remote devices.
A key part of the IGEL OS is the ability to repurpose existing devices into thin clients to prolong the lifecycle of those devices when moving to a digital workspace.

10ZiG Technology provides cutting-edge thin clients and zero clients for the latest virtual desktop infrastructure solutions such as VMware, Citrix, and Microsoft AVD.
Whereas Amulet Hotkey provide devices and IGEL provides the thin client operating system, 10ZiG offers both a range of devices and the operating system that runs on them.
Supporting technology solutions
Security Solutions
When implementing digital workspace solutions whereby you’re allowing users and maybe even customers to access your apps and data, you need to have security at the top of your must have solutions to complement the digital workspace.
Secure access service edge (SASE) is a cloud-based enterprise security framework designed to address the network and security challenges caused by digital transformation. The move to the cloud, coupled with remote users, places not only those users but also devices, applications, and data outside the control of the enterprise data centre and network. Introduced by Gartner, the SASE model responds to this new threat, delivering networking and network security controls at the data centre level, at the edge, and as close as possible to the users, given this is the highest area of risk.
SASE solutions are typically provided by the networking companies such as:
- Palo Alto Networks
- Barracuda Networks
- Akamai
- Cisco
- Fortinet
- Zscaler
Authentication Services
Authentication services are a crucial component of cybersecurity and information technology systems. They’re used to verify the identity of users or entities attempting to access a network, system, or application. Authentication services ensure that only authorised users or devices are granted access while preventing unauthorised parties.
Authentication could be as simple as requiring a password and enforcing strong passwords, or it could be a multi-factor (MFA) solution that uses a password and a code generated by a token or one-time passcode sent to a mobile device via an authenticator application.
Authentication solutions providers include:
- Microsoft Entra ID
- Duo (Cisco)
- Okta
- RSA SecureID
- CrowdStrike
- Yubico (Yubikey)
Workspace Portals
We’ve already mentioned VMware Workspace ONE and Citrix StoreFront/Workspace App. However, there are alternatives such as Liquit. The Liquit Workspace Solution is a software platform designed for delivering and accessing all applications and services in an organisation through a modern workplace. End users access the required applications through a fully customisable, single sign on interface
Management solutions
We’ve talked about some of the proactive management, monitoring, and lifecycle tools when we looked at the assessment phases of the digital transformation and then touched on device management tools in the management phase discussion.
However, a couple of other management platforms should be in scope for your digital transformation project.
Management Studio helps organisations to plan, manage and execute large IT transformation programmes.
It starts with data capture, allowing you to add control by putting context around business decisions and creating automated workflows. Finally, the solution moves to the communication phase to ensure stakeholders and end users are updated on projects. In turn, that allows collaboration with all those involved in the digital transformation project.

We’ve already talked a lot about management solutions for assessment and the ongoing management of on-premises solutions, but with the explosive growth of Microsoft AVD (Azure Virtual Desktops), it’s worth discussing the Nerdio solution.
Nerdio helps by accelerating deployment, minimising costs, and reducing the complexity of cloud-delivered Windows and Windows applications. It does this by wrapping around all the components needed to realise all the benefits of DaaS using AVD. Components such as image management, security and compliance, optimisation, monitoring, and an end user portal.
The solution vendors covered in this document are not an exhaustive list, and we have listed just some of the key technologies for delivering digital transformation. That is especially true when you start to look at SaaS-based solutions, of which there are many to choose from.
Over time, we will build on this list and create a directory of the available solutions and why you should consider one over another, plus any future enhancements that will be implemented over time.
For now, though, this gives you a good starting point to look at the core technologies on offer.

5. Proving the solution
Now that you have the business case, the assessment data, and have identified potential solutions, the next phase is to take a shortlist of those solutions and put them to the test to ensure they deliver against the project goals and objectives.
But before you get carried away with technology and start testing and installing solutions, there’s one crucial thing to do first – define the success criteria.
Success criteria
The success criteria are a documented set of definitions, written down and agreed upon before you start, of what a successful solution should look like. The individual criteria are made up of the key points that the solution must deliver. They can then be used to demonstrate that the chosen solution can successfully deliver against the set criteria. Think of it as a form of acceptance testing, but early on in the testing cycle, as this phase is all about whether the selected solutions are fit for purpose in your environment. For example, you may need a solution allowing end users remote access using their personal devices.
An important factor when defining success criteria is ensuring you get the end users and sponsors to sign up to them. You will need their help understanding whether the criteria have been successfully met. This is also a common mistake that gets made. For example, the IT team installs a new application onto a desktop or delivers it in a new way, opens it, carries out a few basic tasks, and then closes the application and signs it off as successful and working. However, when the end user launches the same application, and as an experienced user, tries out more advanced features, the application fails!
This is particularly true of complex apps such as CAD/CAM or other engineering drawing tools. The CAD application opens without issue, and you can load a drawing; however, when you start to rotate the drawing as a 3D model, for example, the performance is poor and doesn’t deliver an experience that enables the user to be more productive.
Another thing that success criteria provide is to set boundaries so that you do not experience scope creep. Scope creep is when other criteria not appearing on the original list are added. They’re being tested just for the sake of it. You need to firmly stick to the list of success criteria. It doesn’t get tested if it is not defined on the list. It is as simple as that!
The danger of adding new criteria is that the project will be delayed. It could also highlight that you need to revisit the end user engagement, as there should not be any surprises at this stage.
Your success criteria will also influence the technology that you deploy in that you will need to work with solutions that can deliver the success criteria. You would only consider solutions that satisfy the end users and business’s needs and requirements.
The testing phase
When it comes to the testing phase, there are three types of testing we’re going to discuss:
(POC)
(POT)
In the following sections, we will discuss these phases in more detail, what makes each one different, and how you should approach them.
Proof of Concept
A proof of concept is typically a small-scale test setup that remains within the confines of the IT team and doesn’t involve actual end users. Instead, the IT team members take on the role of the end users.
The proof of concept aims to demonstrate whether the solution works and for the IT teams to become familiar with it.
Quite often, a proof of concept is not required. This is particularly true with some digital workspace solutions that have been around as a technology for a long time now and are, therefore, not regarded as a concept anymore. If you’re looking for more “bleeding edge” technology, then a proof of concept may be the way forward.
However, some organisations will still want to conduct a POC regardless, as the technology is new to them, and they want to get a better handle on it. Also, remember that a proof of concept can be time-consuming and that your organisation may be unable to stand something up.
If you can bypass the proof-of-concept stage altogether and move straight to a pilot, then this will aid the speed of the project but will also get end users engaged earlier on in the testing phase. A demo or an extended hosted demo may suffice to get a feel for the solution. Ask the solution vendor to provide details of other similar customers that you can talk to or look at published reference case studies.
There’s also sometimes the risk that a proof of concept is undertaken without a business case. So, at the end of the proof of concept, the project stalls because there was no justification. It was just the IT teams testing technology for technology’s sake. This will happen if the proof of concept is not aligned with the requirements, the business case, or the success criteria.
Proof of Technology
A proof of technology determines whether the proposed solution or technology you want to deploy integrates and is compatible with your current environment.
It is typically used when you have non-standard or bespoke technology and systems deployed within your organisation. The proof of technology would be explicitly designed to demonstrate that these solutions all work together. Therefore, they should be limited to just these niche use cases to ensure they work.
For example, you may have an expensive piece of manufacturing hardware that needs to be connected. So, the proof of technology should be designed to demonstrate that this works correctly and as expected. You may also need to involve end users in this to ensure every aspect of the solution is compatible.
You should think of proof of technology as a technical validation exercise; do not limit this to the IT teams. If you’re dealing with bespoke systems, getting the end user validation is even more critical.
Pilot
A pilot refers to a small-scale rollout of the solution in a production-style environment to real users, showing a limited scope of the intended final solution. The scope may be limited by the number of users accessing the pilot system, the business processes affected, or the business partners involved. The purpose of a pilot is to test, in a production-like environment, whether the solution will deliver the requirements as it was designed to while limiting business exposure and risk. It should be considered as a mini project in its own right and follows its own design, deploy, test, and review phases:
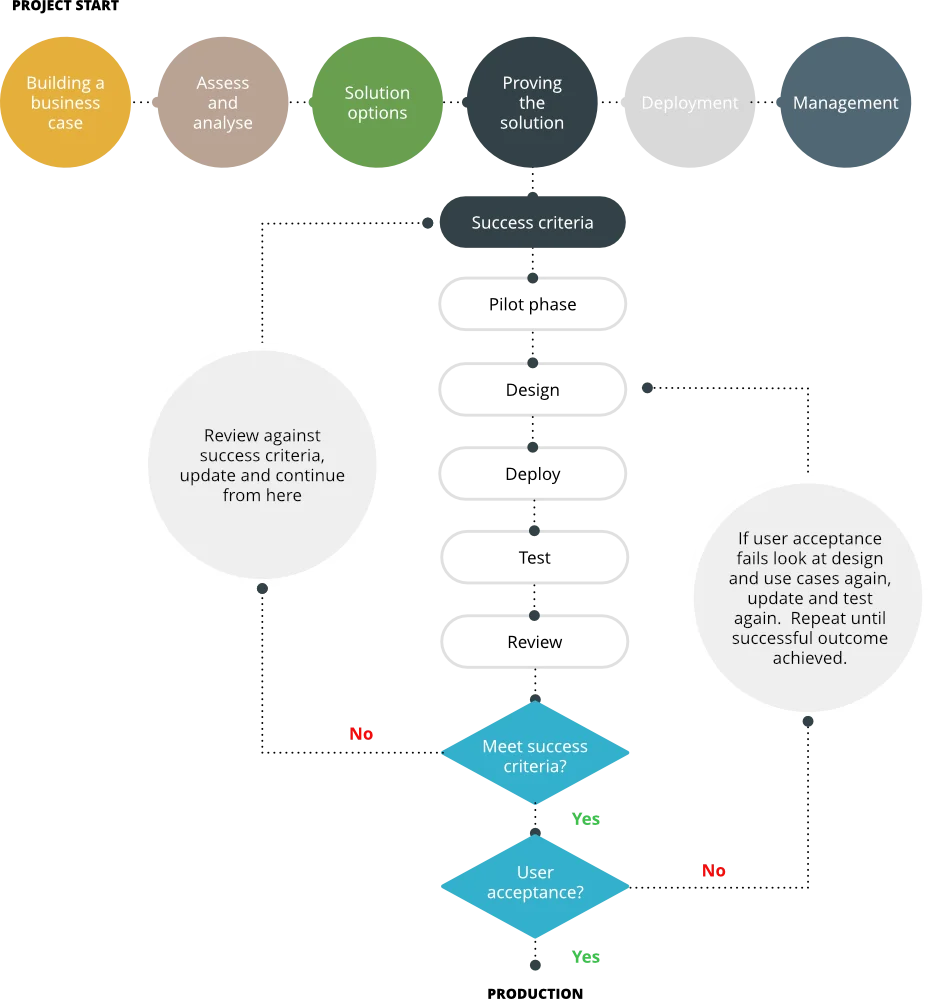
Ideally, and if possible, you should jump straight to the pilot phase. The reason is that you’re working with real-life end users during the pilot stage. This will give you the most valuable feedback and ensure better project progress.
The pilot will give you the feedback you need to see if the project will succeed, as you will essentially be rolling out a small-scale deployment rather than testing in the confines and safety of the IT department or just testing a particular niche use case.
Although the pilot will be a small-scale version of what you will likely deploy in production, you should limit its scope to a small number of end users from each department using the production solution. This ensures you get good coverage of the different business areas and how they work while limiting the risk and exposure to the business. They will also have different use cases.
As previously discussed, your sponsors will play a key role in the pilot. They should be on hand to answer questions from the end users and gain valuable feedback that can be fed back to the design team to ensure the new solution delivers on all end user requirements. Taking this feedback directly from those end users using the solution will ensure the project doesn’t fail. Just so long as you take that feedback onboard and make any necessary changes.
Like the final production design for deployment, the pilot needs to be correctly scoped, sized, and implemented. There’s no point in delivering a pilot that doesn’t match the end solution. If that’s the case, you may need to rerun the pilot. You should approach the pilot this way for several reasons, which we will discuss in more detail in the following sections.
Designing and deploying a pilot
When designing and deploying the pilot environment, you should try to use the same hardware platforms (servers, storage, networking) that you’re planning on using in your production solution. As much as you’re testing the end user experience during the pilot, it is also important to ensure you test the infrastructure. If you’re looking at consuming a cloud platform, then make sure again that any resources you will consume match what will be deployed in production.
A danger with cloud resources, particularly with cloud-hosted desktops, is that because this is a pilot, you pay for the smallest configuration possible due to not wanting to waste your funding. While it is OK to prove functionality, any end users that use the solution during the pilot, which they absolutely should, will possibly report poor performance or end user experience.
We see a couple of common issues with the design and deployment of pilot environments that run on-premises. The first is that the IT team uses any old, unused hardware lying around to install the pilot. Although cost-effective, it won’t give you an indication of how the production environment will perform. You might then go on to purchase new and different hardware for production only to find there’s an issue due to the platform differences or something isn’t supported. You need to pilot end users and infrastructure.
The second issue we see is that once the pilot has been completed successfully, you keep on using it. It suddenly becomes production so as not to disrupt your end users. While this may seem like a good thing to do, as a pilot is a small-scale deployment, how will it cope with scaling? The pilot will have been sized for a limited number of users only. I have seen examples where more and more users are added to a pilot deployment that has crept into production until it breaks and no longer works.
If the plan is to take the pilot deployment straight into production, then you should design it for production from the start, just maybe on a smaller scale. This again goes back to ensuring you’re using the right infrastructure foundations.
Reviewing the pilot
It may sound obvious, but once the pilot phase has concluded, you now need to measure the results against the success criteria to ensure that the solution is fit for purpose and delivers on all the end user requirements. This often gets overlooked, and, as we described earlier, the solution just continues being used as is, given that end users are using it.
First, you need to ensure that it delivered against those success criteria. If it didn’t, you need to understand why not. Was some particular use case missed, or have some end user requirements changed since the pilot was designed and deployed?
It may be more than a perception issue that can be fixed by talking to the end user, although this should not happen if you have your sponsors in place. Regardless, the issue needs to be corrected. Once fixed, the pilot rerun for that particular use case to ensure it is now successful.
Once proven successful, you must get sign-off and agreement that all the end user requirements have been met. Then, and only then, can you move on to the next steps in the project.
Proving the solution does exactly that. It takes the solution(s) that you’ve selected, based on delivering the requirements set out in the business case and considering how end users consume IT services today, and puts them to the test.
The entire process should be treated as a mini project in its own right, with careful thought to the design of any test environment. Above all else, they should have a clearly defined set of success criteria that everyone has signed up to. Without that, it won’t be easy to move on to the next phase of the digital transformation.

6. Deployment
By the end of this stage, you’ll have conducted and completed the deployment. In reality, deployment in this context is the umbrella term used for several different steps and tasks. It starts with sizing, designing, and architecting the solution for your digital transformation project. It finishes once employees are fully onboarded and consuming the new resources.
But that isn’t really the end, given that you still need to continuously review and refine the solution against every changing business and end user requirement.
Before getting started, it is worth looking at how you will manage the deployment process, given this is a complete project in its own right. Therefore, you should follow some formalised project process such as the Agile Scrum Methodology. This enables you to take the various tasks and break them into manageable chunks and also provides check-in points for the key milestones.
Avoid the “big bang” approach to deployment. If possible, gradually phase in the changes, as this won’t disrupt the end users. It also lets you test each key phase or milestone and ensure it works before moving on to the next phase. This will help if you need to troubleshoot something that didn’t quite go to plan.
Stages and elements of deployment
1. Architecture design
The architecture design phase is all about what the solution will look like and starts to get that design documented and signed off. The objective is to look at what components of the selected solution you need to deploy to meet the business requirements and how they will all fit together. Most of this information will have come from your pilot, and realistically, that will have helped define the foundations of the architecture.
The main focus will be on the core solution. For example, it may be a VMware Horizon deployment; however, you also need to include supporting technologies within the design, such as any database requirements, authentication services such as directory services, or additional networking components such as load balancers.
As part of the architecture design, you must include sizing as part of the same exercise, which may dictate additional architecture. For example, you may need more servers to accommodate and service the end user resource requirements. Therefore, that would dictate a change to the architecture design with the need for more compute resources, which in turn might change the storage and network requirements.
As the pilot phase will essentially have been your minimum viable product (MVP), you will now need to make it enterprise-ready. By that, we mean designing in high availability, business continuity, backup, and disaster recovery features.
That could mean further compute resource to add more nodes to a cluster, how data will be backed up, and how to fail over to another site if it goes wrong. Of course, if you’re taking advantage of hosted solutions, the service provider will likely provide those services, but you need to check what they offer and how much they cost.
It is useful at this stage to define your recovery point objectives (RPO) and recovery time objectives (RTO). I.e., where do you want to recover to (what point in time is acceptable to the business), and how long should recovery take before full service is back online?
These should all be discussed with the business as each carries a cost, but you need to understand the cost versus the risk of not operating as a business and the money lost as a result.
2. Sizing
With sizing, it is all about ensuring you design the solution with the appropriate resources required, plus any calculated growth over the next few years. The baseline information for sizing and current resource usage will have been gathered in the assessment phase.
We have already highlighted the danger of taking a pilot solution into production. However, if you have sized the pilot correctly, then you should be able to scale it up so that it meets the production requirements following the steps we will discuss in this section.
Now that you have selected the solution that you will deploy as your digital transformation solution and armed with the assessment data, you can start to size the solution to fit your requirements.
If you’re looking at on-premises solutions, we’re talking about sizing infrastructure such as servers, storage, and networking to support the chosen solution. Then, go down to the next level and look at CPU and memory requirements for end users and applications.
Don’t forget to include any supporting technologies within the sizing exercise. For example, When it comes to cloud-based solutions, you need to look at the predefined sizes on offer, often called T-shirt sizes. Match those to the requirements and, in this case, the pricing to meet the budget requirements.
3. Bill of materials and purchasing
Although this doesn’t sound like an actual deployment-related subject, you will need to purchase the solution components now you know what you need, how many you need, and the size required. This could be written as a bill of materials or a shopping list that purchasing can use to procure the solution components or procure the appropriate subscription services if you’re deploying cloud-based solutions.
This may be a straightforward purchase, or with some organisations, given the size of the solution, it may mean that your purchasing team will go out to tender. Bear this in mind when you factor in time scales for deployment, as the tender process may take some time to complete. Once awarded, there may be additional lead times to factor in.
You may also need to deal with more than one vendor or supplier if the solution comprises different components such as hardware, software, or even services.
4. Build and configure
Following your project methodology, you can start building the solution now that components have been procured.
This should also be broken down into phases rather than deploying everything in one hit and adding your users. This allows you to test each phase of the deployment of the solution before moving on to the next.
For example, build, configure, and deploy the server infrastructure, testing as you go while ensuring what you’re building will meet the project goals and objectives. Then, move on to application deployment, following the same methodology.
This also helps with troubleshooting should something not work as expected. If you complete everything and encounter a problem, it may be difficult and time-consuming to identify where it lies.
Once everything is built, you can start integrating it into the wider environment. Don’t forget also that the build may not be limited to infrastructure. You may be deploying new endpoint devices or other hardware. Now is the time to build those ready for starting the onboarding process.
5. Integration
Now is also the time to start bringing in the supporting technologies and complementary solutions not part of the new digital transformation project.
This means you can now start to integrate essential business applications and tools into the new digital workspace platform. These may be new as well, or they may already exist. For example, integrating directory services so that end users can log in, consume services and access what they need to perform their job roles or add specific hardware.
Testing as you work through the integration is also key, as well as getting end users engaged so that they can verify that everything is working as expected.
6. Migration
Migration goes hand-in-hand with the integration; the objective is to migrate the components required from the existing system. It is worthwhile performing housekeeping tasks on the current data to remove what is no longer needed or irrelevant.
In this phase, you should plan and execute the migration of data, documents, and other required settings to the new digital workspace. Also, look at things like role-based access and other policy-driven rules to ensure end users still have access to what they need.
7. Optimisation
At this stage of the deployment phase, you will have completed the actual deployment regarding everything being built and configured, along with any data migrated (if required) from existing platforms. You should now look to perform optimisation tasks to ensure the end users get the best user experience possible and iron out any performance-related issues.
This is where the tools used in the assessment phase will come into play again as part of the continued lifecycle of the solution and the end users. Remember that we said these tools will have created a baseline as part of the assessment. This baseline can now be used to measure against today’s performance to ensure everything is running optimally and demonstrate the improvements. This will highlight potential performance issues and suggest any changes you can make to enhance the overall end user experience.
8. Testing and QA
Once optimised, you can really start to put the solution through its paces. You should create comprehensive test plans to ensure every solution component is tested before moving into production.
This is where your user groups and departmental champions will again come into play. They can test the systems from the perspective of real users to ensure everything is working as expected. Get them to sign off on being happy with the solution.
Testing could also include any regulatory compliance testing that may be required. You may be a defence company and need Tempest testing, or maybe some form of penetration testing is required. Now that the solution is ready, it is time to complete that before going live.
9. Documentation
Different levels of documentation are required. Obviously, you will have the architectural documents along with the design documents, but also consider creating technical guides on how to build and install the solution. This will help new IT staff if people who design and implement the solution move on to new roles. The solution will still need to be managed, maintained, and supported. It will also serve to demonstrate why something was deployed in a certain way.
Also, consider where you will store the documentation. You could use an online tool such as Confluence.
You should also create documentation and user guides to help the end users navigate and troubleshoot common issues with the digital workspace or how to use it. Consider building Wiki pages or something similar that are non-technical and easy to read and follow.
10. Training and onboarding
Before letting your workforce loose on the new platform, you should provide training sessions on how it works and what it delivers. Let them actually “play” with it before using it in production. This familiarisation will help answer questions now rather than later when they could potentially become support calls!
As with other measured approaches, onboard users in small groups or by department. Don’t go for a big-bang approach. This lets you closely monitor the onboarding and quickly iron out teething problems. Where possible, ensure that you’re physically on hand to answer users’ questions and fix issues as they arise or provide some additional training.
11. Feedback
With the solution now in production and being used by your organisation, you would think that would be the end of the deployment. However, you can continue to do a couple of other things. The first is gathering feedback from users and stakeholders to ensure the solution still delivers against the business case and requirement.
You should then take that feedback and make any necessary improvements and adjustments. This leads to the review and iteration phase.
12. Review and iteration
We said at the beginning that even though the solution has been deployed and is in production, you haven’t really finished. You should continually conduct regular reviews of the digital workspace deployment to identify areas for improvement and ensure it continues to meet organisational goals and business objectives.
The solution can then evolve with your business as it grows rather than you wait for a few years and then have a much larger catch-up project to run. This way, by considering the feedback and reviews, you can make smaller, more cost-effective changes as business demands change.
This document has outlined some key steps and considerations for deploying your digital workspace solution. It covered the sizing, architecture design and purchasing at the start of the deployment phase, right through to onboarding and training the end users.
Remember that the specific steps and tools required for digital workspace deployment may vary depending on your organisation’s size, industry, and unique requirements. It’s essential to involve IT professionals with expertise in digital workspace deployment to ensure a successful implementation.

7. Ongoing management
The final part of our framework for digital transformation is going to look into how to manage the newly deployed solution.
Digital workspace management refers to the process of managing and optimising the digital tools, resources, and environments that employees use to perform their work. It encompasses a wide range of technologies and practices to improve productivity, collaboration, security, and user experience within a digital work environment.
Key aspects of digital workspace management
1. Resource provisioning
Managing resource provisioning involves ensuring that employees have the necessary hardware, software, and access permissions to perform their job roles effectively and productively.
You need to ensure that everything has been configured correctly and has the right amount of compute power, storage, and network connectivity to perform as required, as well as ensure the workforce is equipped with appropriate endpoint devices and remote access.
As time goes by, you might need to add additional resources to cater for updated systems, new applications, and to accommodate workforce growth. So, monitoring resource consumption and usage is key, regardless of consuming on-premises or cloud-based solutions.
2. Application management
Ensuring employees have access to the right software applications and tools is crucial. This involves software deployment, updates, licensing, and monitoring application usage.
It may be useful to deploy some form of software asset management solution to track license usage and version control to understand when updates become available and old versions go end of life, and therefore are no longer supported.
The subject of feedback is also applicable to application management. A new version of an application may become available, but the end users may not want that new version yet as they’d need additional training or a feature they use is no longer available. Make sure you understand the implications of changing any applications, or even operating systems for that matter. It could affect end user productivity.
The final point is to always test any application upgrades with a small subset of users before deploying to a broader audience. Another aspect is licensing costs. Ensure you have the appropriate licensing in place and aren’t paying for licenses for things you’re not using.
3. Security updates
Security updates are patches or fixes released by software developers and vendors to address vulnerabilities or weaknesses in their software or hardware products. These updates are essential for maintaining the security of your computer systems, mobile devices, and software applications.
Therefore, maintaining the security of digital workspaces is paramount, especially when remote users potentially use non-company devices to access data. It includes implementing security policies, access controls, encryption, and threat detection to protect sensitive data and prevent unauthorised access.
This could also form part of maintaining your compliance and regulation certification.
Again, thoroughly test security updates before applying them to a production environment.
Previously, when discussing application management, we touched on old versions of software and operating systems no longer being supported. So, it’s important to note when vendors stop providing security updates for these older versions of their products. Typically, even though a solution or particular version of that solution is no longer available to buy, support will continue for an extended period of time. This means that security patches will still be made available during that period, or you may be able to purchase extended support. Either way, when this happens, upgrading to a supported version or finding an alternative supported solution is crucial.
4. User experience
The most important thing in any end user-focused solution is the user experience. Focusing on the user experience is essential for digital workspace management. It involves ensuring that everything the end users need to do their job is available, works well, and is easy to use.
It also needs to remain that way and goes hand-in-hand with performance monitoring. Just because the infrastructure is running well, don’t assume the end user’s experience is also good.
You will have used tools during the assessment phase that collected data based on that user experience. Now is the time to use those tools to monitor how end users interact with the systems; they can access everything they need, and the systems are responsive.
The minute this isn’t the case, then it is likely the end user will log support calls. Proactively monitoring the end user experience will mitigate these support calls, as you can see any issues before the end users do. Also, think about adding things that help the users. Something like a self-service password reset facility will often stop many support calls and allow end users to do this themselves. This may well be part of the overall objectives of the digital transformation project.
5. Performance monitoring
Continuously monitor the performance of digital workspaces to identify and resolve issues that may affect productivity. This includes monitoring network performance, server health, and application responsiveness.
Having a real-time dashboard view of the system is a key requirement. Ideally, you will still be using the same tools that you used for the assessment phase, which will provide you with an overview of how the system is performing.
6. Device management
This is likely part of your digital transformation project, especially if you have remote users. However, if not, you need to consider how to manage mobile devices, especially those that are personally owned and used to access company applications and data.
This could include devices such as smartphones, tablets, personally owned laptops, and Apple macOS devices. Whatever they’re, you must ensure they’re secure, compliant with company policies, and can access necessary resources.
For example, some solutions can check the device’s security posture, and any devices deemed unsafe (running a very old version of an operating system, for example) will be prevented from connecting. There are also other benefits to device management solutions, such as seamless onboarding of end users without them needing to come to the office or remotely wiping compromised devices. Again, this could be part of your overall digital transformation project.
7. Cloud management
Cloud management refers to monitoring, optimising, and controlling cloud resources and services. It is often referred to as a Cloud Management Platform (CMP). It involves the management of all aspects of cloud computing, including infrastructure, applications, and data, to ensure that they operate efficiently, securely, and cost-effectively.
Cloud management is crucial for organisations that rely on cloud services to run their IT operations because it will help them maximise the benefits of the cloud while minimising potential risks and costs.
It will include all the topics discussed in this document, such as resource provisioning, scaling, security, and performance monitoring, but aimed at cloud-based solutions.
8. Change management
Change management refers to the structured approach and set of processes an organisation uses to transition from its current state to a desired future state. It involves planning, implementing, and monitoring changes to ensure they’re effectively adopted and result in improved outcomes. Change management is crucial in various contexts, including organisational change, technology implementations, and process improvements.
As part of the overall management of the digital transformation solution, you will have already worked through several changes. Still, as part of the ongoing management, you should focus primarily on improvements.
Any changes will culminate with feedback from end users and be based on monitoring and lifecycle management of the solution elements.
9. User support
End user support typically involves setting up systems and processes to provide assistance and resolve issues for the end users of the digital workspace. You may well have deployed a support tool as part of the transformation project, but if not, then you need to consider the following:
- Define Objectives: Clearly outline the goals and objectives of your end user support initiative. Define the level of support you want to provide and the key performance indicators (KPIs) to measure whether end user resolution has been successful.
- Create Support Channels: Establish communication channels for end users to seek assistance. Common support channels include email, phone, live chat, a ticketing system, and self-service portals.
- Hire and Train Support Staff: Recruit and train support staff knowledgeable about the deployed solution and capable of providing effective assistance to end users. Training should cover product knowledge, communication skills, and problem-solving techniques.
- Develop Knowledge Base: Create a comprehensive knowledge base with FAQs, troubleshooting guides, and how-to articles. This can help users find answers to common questions without contacting support.
- Set Service Levels: Define service level agreements (SLAs) that specify response and resolution times for different types of support requests. Ensure that these SLAs are realistic and achievable. For example, priority one could be a server down. Therefore, a 4-hour fix is required, whereas an end user issue might be much lower and doesn’t stop them from working, so 48 hours might be acceptable.
- Implement Ticketing System: If applicable, set up a ticketing system to track and prioritise support requests based on defined SLAs. This helps ensure that requests are handled promptly and not lost or overlooked.
- Self-Service Options: Encourage end users to resolve common issues independently through self-service options, such as online guides, tutorials, and FAQs.
- Education & Training: Proactively provide education and training for end users so that they make the most of the solutions available. Don’t just do this on day one when you go live with the new platform. Have a continual development program of training.
- Feedback & QA: Feedback is again important to understand that end user issues are being resolved and end users are satisfied with the service. This potentially goes towards showing KPIs are being met for measuring support. Provide surveys after a support incident, for example. This helps with the continuous improvement of the platform.
10. Maintenance
As with any other IT system, you must perform regular maintenance. This could be ensuring that software such as applications and operating systems are all patched and up to date to ensure you’re running supported versions and taking advantage of new features. As part of the maintenance plan, you should test disaster recovery and business continuity.
11. Feedback
We have already discussed feedback during the assessment phase, but it shouldn’t end there. The best way to understand if everything is still working as expected is to continue that end user interaction.
It might be worth setting up some sort of “suggestions box” where everyone can suggest improvements or highlight changes in how they work that might affect how systems are delivered. Either way, keep the lines of communication open.
12. Compliance and regulation
In many cases, and often depending on your industry, your organisation must establish compliance programs to ensure that you meet all relevant regulations and standards. These programs typically involve processes, policies, and procedures to monitor and enforce compliance within the business. Failure to comply with regulations can result in legal consequences, fines, penalties, and damage to an organisation’s reputation.
Effective compliance and regulation are crucial for maintaining order and protecting the rights and well-being of individuals and society. Businesses and individuals must stay informed about relevant regulations and actively work to ensure compliance to avoid legal and financial repercussions.
As part of managing the solution, you must ensure that these requirements are constantly monitored and that any changes and updates are implemented. For example, you may require ISO 27001 for managing information security or Cyber Essentials. Maybe you work in defence and require specific certifications to work at different classification levels.
13. DR and business continuity
Disaster recovery (DR) is a set of processes, policies, and procedures designed to help you recover and resume normal operations as quickly as possible in the event of a significant and disruptive incident or disaster. These incidents can include natural disasters such as hurricanes, earthquakes, floods or technology-based failures such as hardware failures, software failures, power events, human errors, or other unforeseen events that can disrupt business operations.
This would have been presented as part of the business case and then factored into the design, but now as part of the ongoing management, you need to ensure that it will deliver. Consider it a fire alarm test whereby you practice sounding the fire alarm, ensuring the evacuation process works.
Ensure that you can easily failover to a DR site or that your high-availability features work by proactively and regularly testing them. There’s no point in having DR and business continuity if it fails when called upon.
14. Cost management
Cost management is the process of planning, controlling, and optimising an organisation’s expenses to ensure that resources are allocated efficiently and effectively to achieve its goals and objectives. It is a crucial aspect of overall financial management and is essential for the long-term sustainability and success of any business or organisation.
Effective cost management requires a proactive and continuous effort to control and optimise expenses while aligning them with the organisation’s strategic objectives. It involves collaboration across different departments and organisational functions and is critical to financial stewardship and business success.
Overall, digital workspace management is about creating an efficient, secure, cost-effective, and user-friendly digital environment for employees to work effectively.
It requires a combination of technology, policies, and best practices to achieve these objectives, as well as continual review and improvement. This ensures that the digital platform still delivers against the business case, or conversely, the ongoing management dictates an update to the business case to ensure the platform remains relevant and still delivers business requirements.

8. Framework Summary
With the digital transformation framework, we’ve put together some key steps for successfully navigating the digital transformation journey for your organisation.
It all starts with building a solid business case to not only get the buy-in of the stakeholders but also to secure the budget to take the project from the drawing board to reality.
The next steps involve getting a better understanding of your current environment. It can be described as assessing the “five W’s” of your organisation’s environment: Who, what, where, why, and when.
Once you understand this, you can look at the technology solution options that meet the objective of the business requirements as defined in the business case and the end user requirements.
Having selected the appropriate solutions, you can start to put them through their paces with clearly defined success criteria so that you can clearly demonstrate that the solutions meet the business and user requirements. Multiple options meet the brief, in which case it could come down to cost and ongoing management. Or that people within your organisation already have experience with one of the options.
Now that you’ve selected and tested the solution you’ll be deploying in production, you can move into the design and deployment phase. This also includes a project plan for deployment, the actual deployment itself, and a number of things you need to think about and plan for.
Theoretically, the final step is delivering ongoing management to ensure the deployed solution is updated and meets any certification and regulatory requirements. You also need to think about ensuring the end user experience is at its optimum and that you have a robust plan for support and delivering services in the event of an outage.
In the previous paragraph, we said “theoretically”; by that, we mean that you haven’t quite finished there. Even though the digital transformation project has been deployed and is being used in production, you need to continually monitor, assess, and improve the solution to ensure that everything is kept updated and is also delivering on the requirements of the business.
We’re not saying you have to start again from the beginning, but continual monitoring and improvement, measuring against requirements, and taking onboard feedback will ensure any digital transformation evolves with the business.

